You can delete AWS Organization in an account through the CLI command below:
aws organizations delete-organization --profile a2
As we have the organization deleted, you would see no organization while navigating to the AWS Organization home page.
Create an organization.
aws organizations create-organization --profile a2
We're not passing anything like name. That means, you can create at most only one organization in an account.
Let's go back to the console.
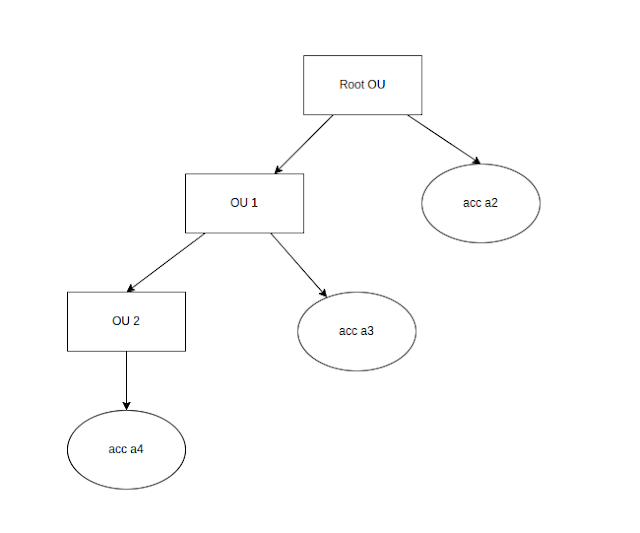
That created an Organization. It contains a Root OU and a member account (current account which is the management account). Each organization has a management account where the features of the organization are configured. In our case, a2 is the management account as we have created the organization in a2 account (current account).
Root is the top most OU (Organizational Unit). An OU, which is a logical grouping of accounts or other OUs, can have either another OU or an account as its child. An OU can have more than one child. An account cannot have a child. Please see the image above to understand about the hierarchy (the tree structure is just one of the many forms your organizational structure can have).
The Service Control Policies (SCPs) applied to Root OU will be applicable to all of its children. SCPs applied to OUs will be applicable to its children e.g., SCP applied to OU1 will be applicable to both acc a3 and acc a4. SCPs applied to individual accounts will be applicable only to those accounts (they won't have children).
Let me try to create another organization in the same account from the terminal.
aws organizations create-organization --profile a2







Comments
Post a Comment